Zero Belief Structure flips the outdated “trusted community” mindset on its head. As an alternative of assuming your internet hosting surroundings is secure, Zero Belief treats each person, system, plugin, API name, and repair as untrusted till confirmed in any other case. When paired with robust internet hosting fundamentals it offers you a sensible path to lock down WordPress, safe microservices, and shield instruments like Discord with out slowing down your web site or irritating your staff. It’s a better, fashionable technique to defend what you are promoting because it grows.
Zero Belief Structure is all over the place in safety conversations at present, but it stays broadly misunderstood. Cloud platforms promote it, distributors declare to allow it, and instruments label themselves Zero Belief-ready. However when groups strive making use of it to actual environments like hosted web sites or SaaS merchandise, the small print get complicated quick.
In case you’re operating an internet site, utility, or inside instrument on hosted infrastructure, you’ve most likely requested: how does Zero Belief truly apply to my surroundings? You’re not securing a company HQ community. You’re securing WordPress websites, shared internet hosting accounts, cloud apps, APIs, microservices, and communication channels like Discord.
The excellent news? Zero Belief completely applies to your world, however not within the simplified means distributors typically describe.
This information breaks Zero Belief down in plain language, exhibits how internet hosting selections form your start line, and descriptions a sensible roadmap you possibly can start utilizing instantly.
Understanding Zero Belief in Plain Language
Conventional safety assumes that after you’re contained in the community, you’re trusted. Zero Belief rejects that concept utterly. No person or system is trusted routinely: each request wants verification, and entry is restricted to solely what’s crucial.
Zero Belief will not be a product you should buy. It’s a technique that influences your internet hosting setup, your functions, and the way your staff manages identification and entry. Distributors provide instruments that help Zero Belief, however no platform delivers it alone. That’s why Zero Belief is particularly related in hosted environments the place you don’t management the bodily community layer.

Why Zero Belief Issues Now for Hosted Apps
Zero Belief jumped from area of interest idea to mainstream necessity as a result of fashionable environments are essentially completely different from conventional workplace networks. Right now’s workloads run throughout shared internet hosting, VPS, cloud, SaaS, and hybrid platforms. Groups function remotely and throughout a number of time zones. Communication occurs on instruments like Discord that weren’t designed with enterprise safety in thoughts. Purposes use APIs and microservices that every want unbiased identification checks. And WordPress faces 13,000 assaults per day, making robust identification controls important.
Trusting a “secure” inside community is now not real looking. Zero Belief offers you an method that works whether or not your belongings dwell on shared internet hosting, managed WordPress, or multi-cloud infrastructure.
How Internet hosting Selections Form Your Zero Belief Technique
Understanding why Zero Belief issues is one factor. Implementing it begins with a sensible query: the place does your infrastructure at present sit? Your internet hosting platform doesn’t decide whether or not you possibly can implement Zero Belief, nevertheless it does outline your start line.
Shared Internet hosting Via a Zero Belief Lens
Shared internet hosting is a standard entry level for small groups. To help Zero Belief ideas, it depends on robust isolation and automatic protections, together with account isolation, Internet Software Firewall (WAF) filtering, DDoS mitigation, and computerized updates and malware scanning.
These built-in controls offer you a foundational layer of Zero Belief with out requiring advanced configuration.
VPS and Cloud Internet hosting for Groups Able to Advance
VPS and cloud internet hosting offer you extra management over segmentation and identification. You’ll be able to design non-public networks, create customized firewall guidelines, join identification instruments like SSO, and outline stronger belief boundaries for microservices or APIs.
Groups with compliance necessities typically function right here as a result of Zero Belief relies upon closely on segmentation and identification administration.
Managed WordPress as a Safe-by-Default Beginning Level
Managed WordPress provides guardrails that align naturally with Zero Belief: computerized updates, hardened PHP settings, real-time scanning, pre-configured WAF guidelines, and secure staging environments. These options offer you a safe baseline while not having deep technical experience.
Actual-World Purposes & Zero Belief: WordPress, Discord & Microservices
Zero Belief works greatest when you possibly can apply it on to your most vital workloads. Understanding the ideas is helpful, however the actual worth comes from implementing them within the particular instruments and platforms your staff makes use of on daily basis. Right here’s how Zero Belief maps to actual hosted environments you’re truly working with.
Zero Belief for WordPress
WordPress advantages straight from Zero Belief ideas. Begin with identification: require MFA, take away unused accounts, keep away from the default “admin” username, and use robust passwords. Apply least privilege by assigning solely crucial roles and disabling file modifying within the dashboard.
Help this with segmentation: restrict entry to wp-admin when potential, separate staging from manufacturing, and use a CDN to soak up malicious site visitors. Steady verification comes from common scans and exercise logging to catch uncommon habits rapidly.
These enhancements strengthen your WordPress safety with out sacrificing efficiency.
Zero Belief for Discord and Group Communication Instruments
Discord is constructed for open communication, not strict safety. Content material sticks round, permissions could be messy, and bots introduce danger. Zero Belief offers you a technique to tighten issues up: require MFA for moderators and employees, take away former workers rapidly, audit roles repeatedly, and restrict what bots can see or do.
If what you are promoting wants strict compliance like HIPAA, PCI, or CMMC, Discord merely can’t meet these necessities as a result of it doesn’t present the verification and audit controls these requirements demand.
Zero Belief for Microservices and APIs
For builders, Zero Belief means each service should show its identification, not simply the gateway. Quick-lived tokens, mTLS between companies, and restricted community entry assist forestall lateral motion. Logging and anomaly monitoring enable you to spot uncommon habits early. Even small apps profit from these fundamentals.
Balancing Zero Belief With Efficiency and Consumer Expertise
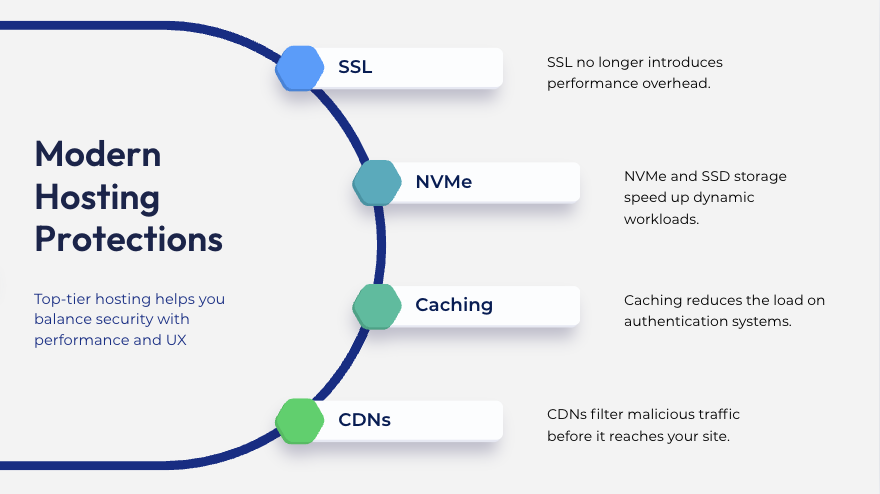
Some groups fear that Zero Belief will gradual all the pieces down. In actuality, fashionable internet hosting makes these protections light-touch:
- SSL now not introduces efficiency overhead.
- NVMe and SSD storage pace up dynamic workloads.
- Caching reduces the load on authentication techniques.
- CDNs filter malicious site visitors earlier than it reaches your web site.
On a well-engineered platform, Zero Belief safety and quick efficiency work collectively, not in opposition to one another.
Reference Fashions: Three Clear Zero Belief Paths
Zero Belief adoption doesn’t occur abruptly. Listed here are actual examples of how groups can method it based mostly on their surroundings.
Small Enterprise on Shared or Managed WordPress
Begin with a safe basis: WAF protections, computerized updates, malware scanning, and DDoS mitigation. Layer on MFA, robust passwords, a staging surroundings, and constant backups. Present fundamental person coaching and overview entry periodically to remain forward of points.
Rising Group on VPS or Cloud
As your wants broaden, create segmented environments, introduce API gateways, implement logging and monitoring, and produce authentication underneath SSO. This provides your staff extra management whereas lowering friction.
Compliance-Pushed Organizations
Compliance-heavy groups require strict identification guidelines, detailed audit logs, encrypted environments, automated certificates administration, and a well-tested incident response plan. That is the place full Zero Belief maturity turns into important.
The best way to Consider Internet hosting Suppliers for Zero Belief Readiness
Ask potential suppliers about:
- Infrastructure controls: buyer isolation, patching practices, built-in DDoS mitigation.
- Safety visibility: entry to logs, malware scanning, WAF protections.
- Help high quality: availability, responsiveness, SLA ensures.
No internet hosting supplier can “do Zero Belief for you,” however the appropriate one makes implementing it a lot simpler.
Zero Belief Implementation Roadmap for Hosted Environments
Right here’s a sensible timeline you possibly can observe. This roadmap builds progressively from fast wins to full Zero Belief adoption and works for groups of any measurement: small enterprise, company, or enterprise.
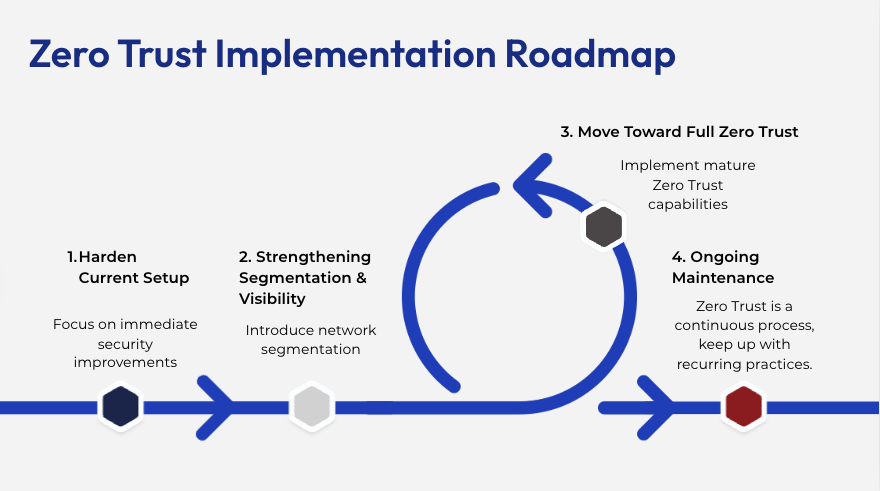
Part 1: Hardening Your Present Setup (0–30 Days)
Deal with speedy safety enhancements you possibly can implement with out altering your infrastructure. These are high-impact, low-friction adjustments that set up your safety baseline.
Identification and Entry Administration
- Allow MFA for all WordPress admin accounts, internet hosting management panels, and communication instruments
- Take away unused accounts throughout WordPress, FTP/SFTP, and databases
- Exchange default “admin” username and require robust passwords (16+ characters)
- Implement password managers throughout your staff
Software program and Patch Administration
- Replace WordPress core, plugins, and themes to newest variations
- Delete unused plugins and themes earlier than updating
- Replace PHP to the newest steady model
- Allow computerized updates the place potential
Backup and Restoration
- Arrange automated every day backups saved off-server
- Check restoring no less than one web site from backup
- Doc restoration procedures and arrange monitoring alerts
Perimeter Protection
- Activate Internet Software Firewall and configure guidelines
- Allow computerized malware scanning (every day minimal)
- Arrange alerts for malware detection
Documentation
- Create an entry stock documenting all admin accounts, internet hosting accounts, and third-party integrations
- Set up a course of for requesting and revoking entry
Part 2: Strengthening Segmentation and Visibility (30–60 Days)
Introduce community segmentation and monitoring capabilities. These adjustments require extra planning however considerably enhance your safety posture.
Community Segmentation
- Limit wp-admin entry by IP handle or VPN
- Configure SSH to require key-based authentication and disable root login
- Create separate staging environments for all manufacturing websites
- Set up a promotion course of from staging to manufacturing
Software Segmentation
- Implement API keys for service-to-service communication
- Use short-lived JWT tokens (15-60 minute expiration)
- Retailer secrets and techniques in surroundings variables or secret managers
Logging and Monitoring
- Allow WordPress exercise logging and server entry logs
- Configure failed login try monitoring and alerts
- Allow file integrity monitoring for important directories
- Set up baseline habits to establish anomalies
SSL/TLS and Database Hardening
- Pressure HTTPS throughout all websites and allow HSTS
- Change default database prefixes and limit entry to localhost
- Commonly rotate database passwords
Fee Limiting
- Configure price limiting on login pages (max 5 makes an attempt per quarter-hour)
- Set price limits on API endpoints
- Allow CDN-based DDoS safety
Part 3: Shifting Towards Full Zero Belief (60–90 Days)
Implement mature Zero Belief capabilities with centralized identification administration, superior monitoring, and automatic safety workflows.
Centralized Identification Administration
- Implement SSO answer (Okta, Auth0, Azure AD)
- Join WordPress, internet hosting management panel, and communication instruments to SSO
- Arrange conditional entry insurance policies based mostly on system/location
Superior Entry Controls
- Create location-based entry guidelines
- Implement system posture checks and risk-based authentication
- Configure time-based entry restrictions for contractors
Service-to-Service Safety
- Deploy mTLS for microservice communication
- Implement API gateway to centralize authentication
- Arrange certificates rotation automation
Incident Response
- Doc incident response procedures for frequent situations (malware, breach, DDoS)
- Conduct tabletop workouts together with your staff
- Check backup restoration underneath time strain
- Outline escalation paths and communication protocols
Automation and Monitoring
- Arrange automated deployment pipelines with safety scanning
- Implement centralized log aggregation and safety dashboards
- Monitor certificates expiration and failed authentication makes an attempt
- Arrange anomaly detection for person habits
Compliance
- Doc all safety controls for audit functions
- Create compliance checklists to your business (HIPAA, PCI, SOC 2)
- Schedule common vulnerability assessments
Part 4: Ongoing Upkeep (90+ Days)
Zero Belief is a steady course of. Set up these recurring practices:
Month-to-month: Overview entry logs, check backup integrity, audit new person accounts, test for software program updates
Quarterly: Conduct formal entry evaluations, check catastrophe restoration procedures, overview price limiting thresholds, replace safety documentation
Annual: Conduct complete safety audit or penetration check, consider internet hosting supplier capabilities, conduct incident response workouts, plan subsequent yr’s safety enhancements
Fast Reference: Precedence Matrix
1. Excessive Impression, Simple to Implement (Do First)
- Allow MFA all over the place
- Take away unused accounts
- Allow computerized backups
- Replace all software program/plugins
- Allow WAF and malware scanning
2. Excessive Impression, Average Problem (Do Second)
- Limit admin entry by IP
- Implement staging environments
- Arrange logging and monitoring
- Configure price limiting
3. Excessive Impression, Excessive Problem (Do Third)
- Implement SSO
- Deploy API gateway
- Arrange superior monitoring/SIEM
- Implement automated CI/CD
- Deploy mTLS for microservices
This roadmap offers a structured path to Zero Belief adoption with out overwhelming your staff. Begin with Part 1, measure your progress, and transfer ahead once you’re prepared. Keep in mind: progress is healthier than perfection, and even partial implementation considerably improves your safety posture.
Last Abstract
Zero Belief will not be a buzzword or a boxed safety product. It’s a sensible architectural method that matches naturally with how fashionable web sites, apps, and digital groups function. Whether or not you’re securing a WordPress web site, managing shared internet hosting accounts, constructing APIs, or operating inside communications on Discord, Zero Belief helps scale back danger whereas conserving your surroundings quick, dependable, and user-friendly.
When paired with a internet hosting basis engineered for pace, uptime, and actual human help, Zero Belief helps you construct a safer platform for what you are promoting to develop on, with out including pointless friction to your staff or prospects.

